Given the amount of business, social interaction, and general slacking that occurs online you would hope the people took data security seriously. Yet, every time you turn your head it seems as if another payment processor or video game developer has been hacked. Even worse, attacks on personal computers has remained high and the general public aren’t sure what to do. So here are a few ways to protect your business, or just yourself.
Encryption
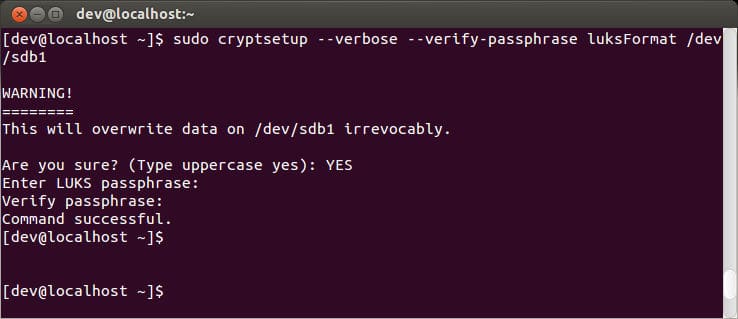
Let’s lead off with something that is applicable to all levels of user, whether enterprise of personal. The encryption of sensitive data that you MUST store on your PC is paramount. Taxes, birth certificate, applications for any sort of credit ever, all of these have moved online. It’s convenient to do, you can sit around naked, and you need not talk to another living person. Therefore, most of us have begun to do it.
Now with that in mind, it’s easy for just anyone to have access to all of that information if they know what they are doing. Just one small lead like a social security number can set someone off an identity stealing tangent and soon enough they’ll be charging thousands of dollars to your credit card. A good way to nip this problem in the bud is to look into data encryption solution. Don’t wait until it’s too late, as it can be nearly impossible to get your identity back if it was stolen by a skillful thief.
The problem, is that these things are giant treasure troves of data. With just a social security number, and a visit to a phone book (or Facebook in these days) someone can steal your identity. Suddenly that dream vacation to Europe is being billed in your name, and experienced by Spencer the smelly college kid. Your credit score tanks quickly as new lines of credit appear, and suddenly you’re left clean up the mess. What’s worse, credit card numbers are so easy to come by that they sell for less than $10 a card on the black market.
Penetration Testing
This goes for our more business savvy readers. Whether you’re running a small embroidery business, a collection of blogs, or a fortune 500 company, you need to be secure. Hiring an off site security firm is the best way to do that. Companies like Egnyte offer third party security firms to perform continual penetration tests, an undervalued service in today’s business world. Consider that a study of office workers showed a failure to update personal devices which produced gaping holes in security and suddenly it becomes a little more apparent. Everyone has a smartphone, and most everyone else has a tablet or a laptop, all of which are gateways into your network.
Two-step security
Now this is a lot more simple than most of you might think, and can apply to all levels of user. At the personal level you might employ a service like Paypal. This service removes the need for you to type, and store, payment information on a useful service such as Steam. In this event if Steam is ever compromised, your credit card isn’t a point of concern.
Conversely, a business might employ several separate networks and user ID’s for authentication. For instance, you might have a local computer login for your users to access their machines, and a separate login and password for all sensitive data. This way you create an easily severed bridge between client info and employee mishaps, and are better able to isolate any intrusions before they become a liability.
Physical Security?
See, here’s the thing… not only are hackers trying to attack you virtually, but physically as well. Allow me to clarify that a little more. If you’re simply throwing your credit card statements in the trash, that makes it easy for would-be thieves to sift through and find it. So protect yourself from all attack. Perhaps install a few security cameras coupled with Livewatch alarm monitoring; even fake cameras are enough to deter an identity thief. At the very least, keep your receptacles in plain sight. However, the absolute easiest thing you can do is have your unwanted documents professional shredded and disposed of properly.
Remember, we live in a digital age and the internet can prove to be a great equalizer for businesses. It can unlock markets you would never have had access to, as well as connect you with talent employees. Yet, like any door it must be guarded and guarded well.